Hello @@Martin Kallukalam,
In Microsoft Entra ID, there is no built-in claim that explicitly returns the custom domain name (like domain1.com, domain2.com, etc.) as a standalone claim in the ID or access token by default—particularly when the user is cloud-only (i.e., created directly in Azure AD without federation).
Hence as a workaround you can extract Domain from UPN or create a custom extension attribute (via Microsoft Graph), assign the domain explicitly to the user, and then expose that claim in the token.
Workaround 1: Extract Domain from UPN
Configure UPN as optional claim:
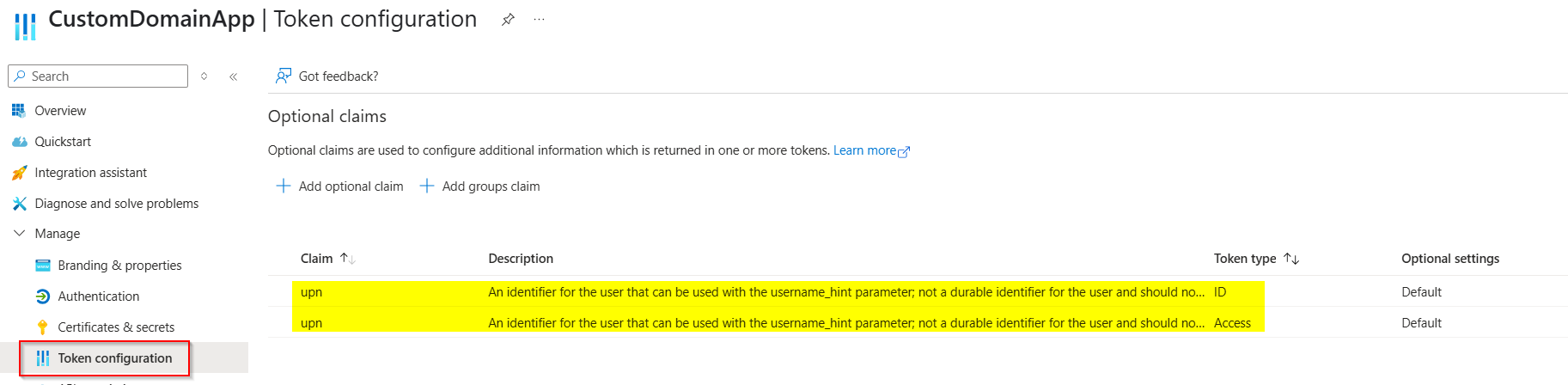
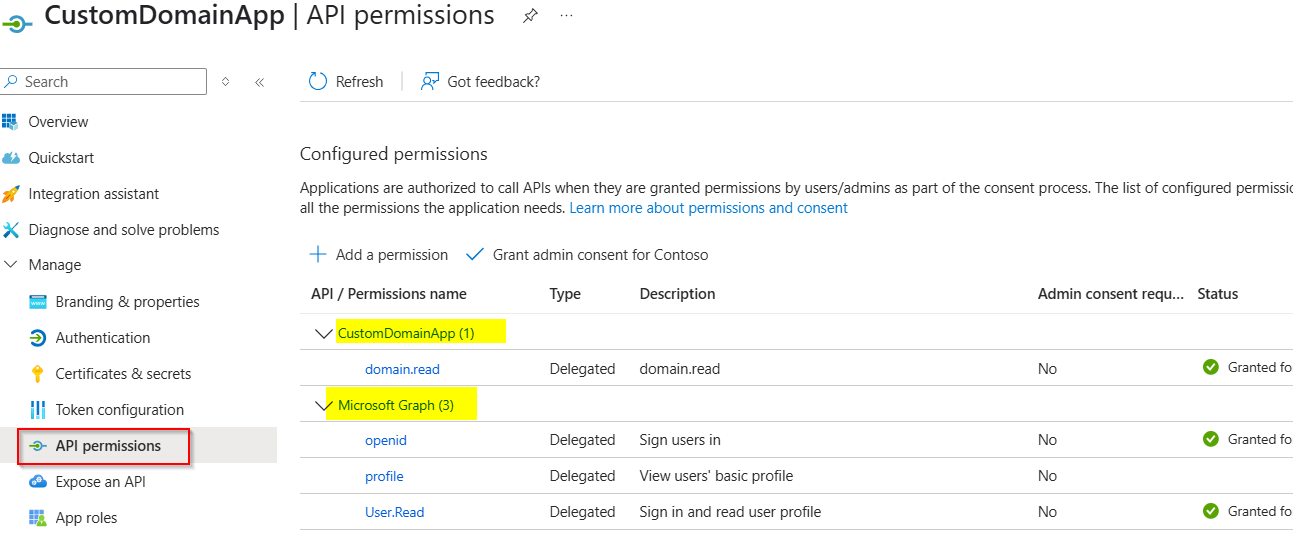
Grant API permissions like below:
Generated access and ID tokens:
GET https://login.microsoftonline.com/organizations/oauth2/v2.0/token
client_id: ClientID
grant_type: authorization_code
scope: api://xxx/domain.read openid
redirect_uri: RedirectURl
code: Code
client_secret: Secret
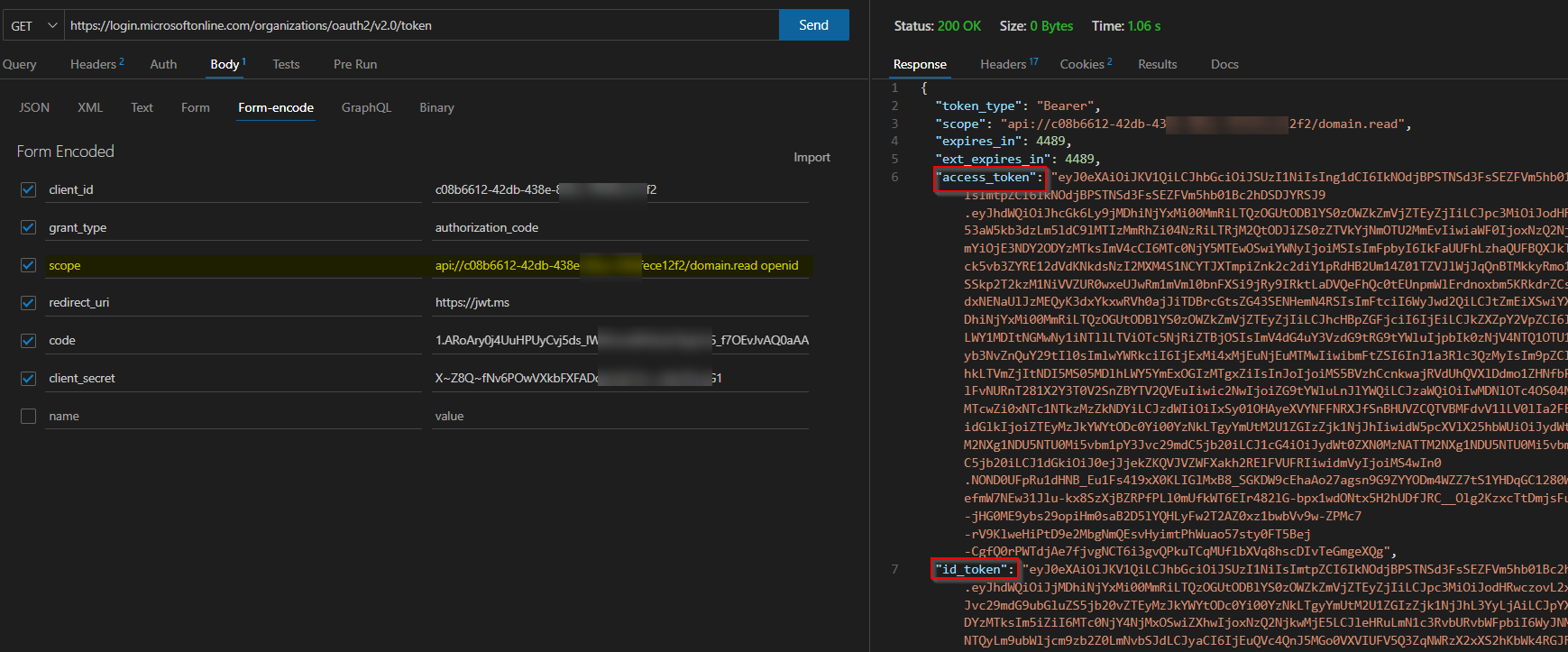
And UPN will be displayed in tokens, and the domain can be extracted in your app logic using string manipulation and you can do this client-side or server-side:
For sample:
const upn = tokenClaims.upn || tokenClaims.preferred_username;
const domain = upn?.split('@')[1];
Access Token:

In ID token also UPN will be displayed.
Workaround 2: Create a custom extension attribute, assign the domain explicitly to the user.
Create a custom extension attribute:
POST https://graph.microsoft.com/v1.0/applications/ObjectID/extensionProperties
Content-Type: application/json
{
"name": "customDomain",
"dataType": "String",
"targetObjects": [ "User" ]
}
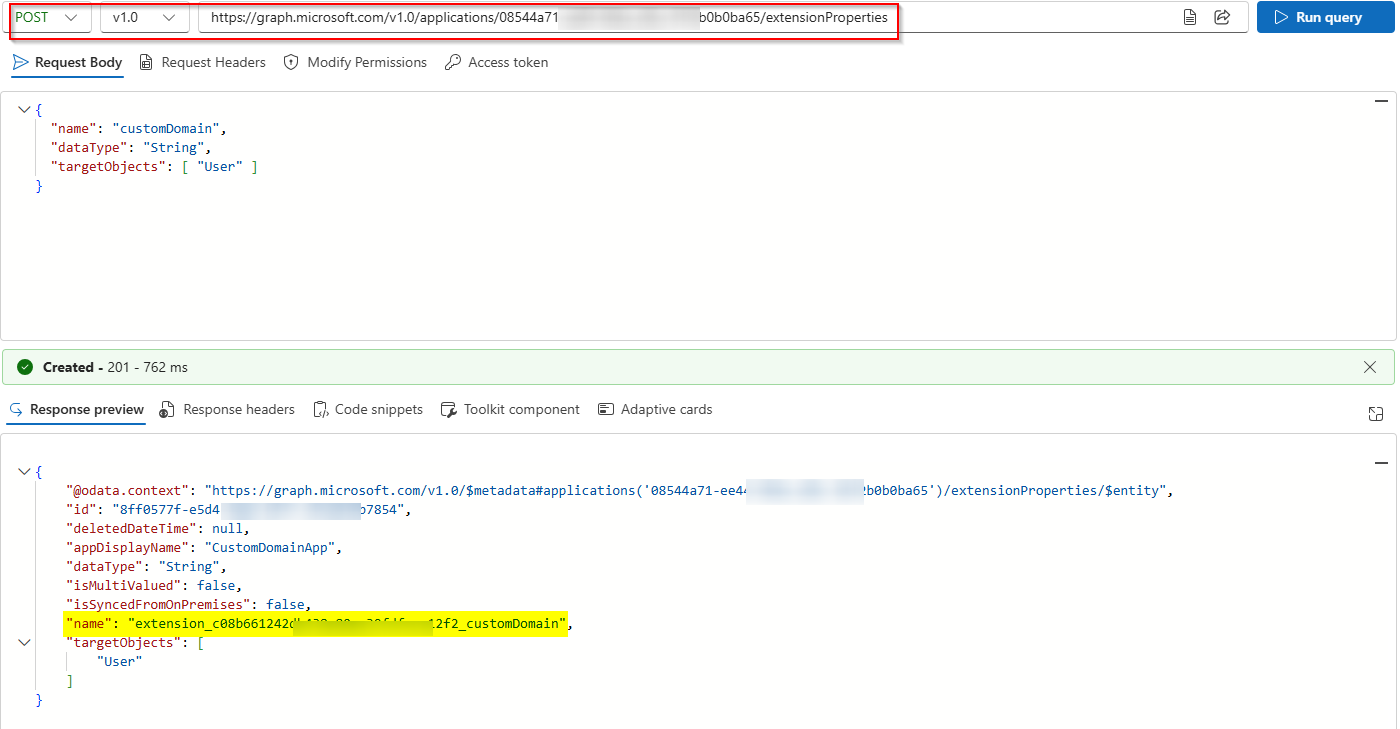
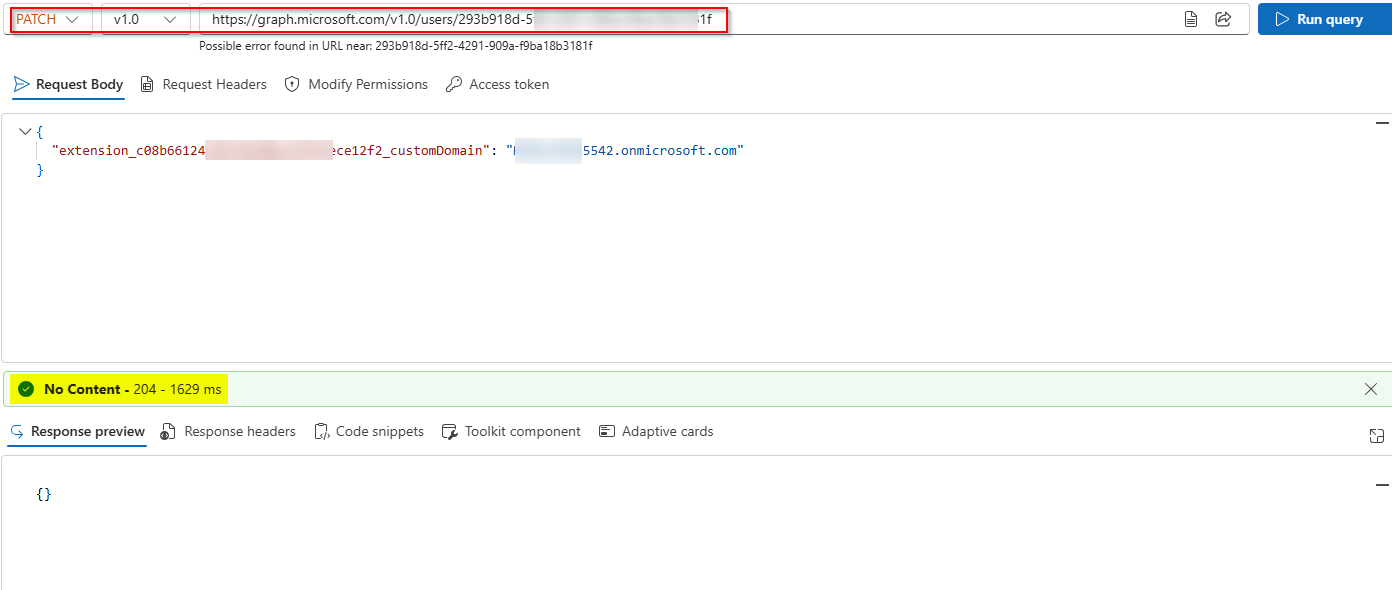
Set the Custom Domain for Each User:
PATCH https://graph.microsoft.com/v1.0/users/UserId
Content-Type: application/json
{
"extension_{appClientId}_customDomain": "domain1.com"
}
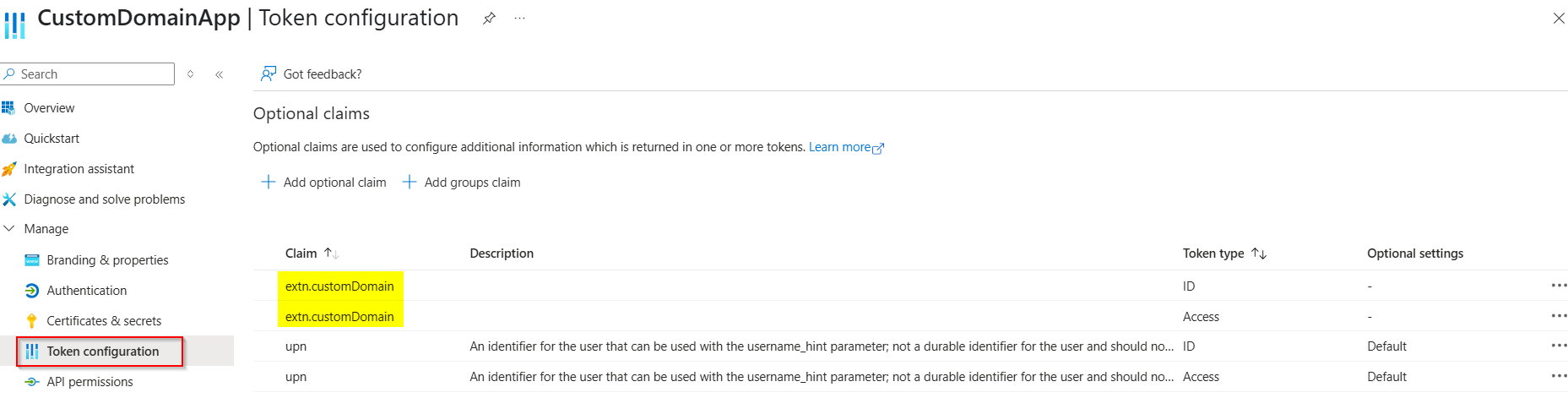
Configure optional claims in Microsoft Entra ID application:
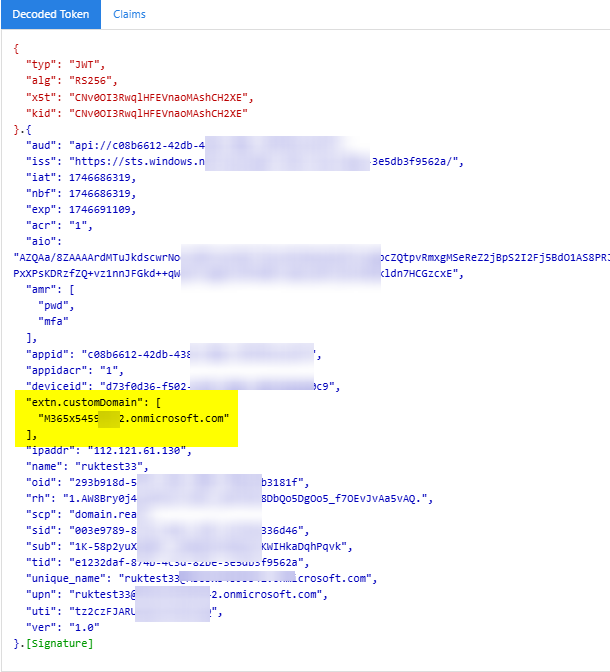
Generated tokens and now you custom claim extn.customDomain in the access and ID tokens:
Access Token
Hope this helps!
Kindly consider upvoting the comment if the information provided is helpful. This can assist other community members in resolving similar issues.