How to enable MQTT broker authentication logs for Azure Event Grid?
I have a problem with connecting intelligent camera to Azure Event Grid MQTT Broker using client certificate.
I'd like to see the detailed debug logs of connection using client certificate of the broker similarly as I can see it on Mosquitto.
In monitoring->Metrics I can only see a connection counts, but no detailed log in text form.
How to configure it?
Pawel
Azure Event Grid
-
Pawel Czop • 20 Reputation points
2025-03-21T10:54:06.22+00:00 Additional information:
Nothing also shows in Monitoring->Logs for Authentication error query, and Session Connections query
-
Khadeer Ali • 4,960 Reputation points • Microsoft External Staff
2025-03-21T12:16:11.5333333+00:00 Thanks for reaching out. Azure Event Grid allows you to monitor and audit data plane interactions of your client applications using runtime audit logs and application metrics logs.
Using Runtime audit logs you can capture aggregated diagnostic information for all data plane access operations such as publishing or consuming events. Application metrics logs capture the aggregated data on certain runtime metrics (such as consumer lag and active connections) related to client applications are connected to Event Grid.
You can enable diagnostic logs by selecting Diagnostic settings from the Monitoring section on the Event Grid namespace page in Azure portal. Select Add diagnostic setting as shown in the following screenshot.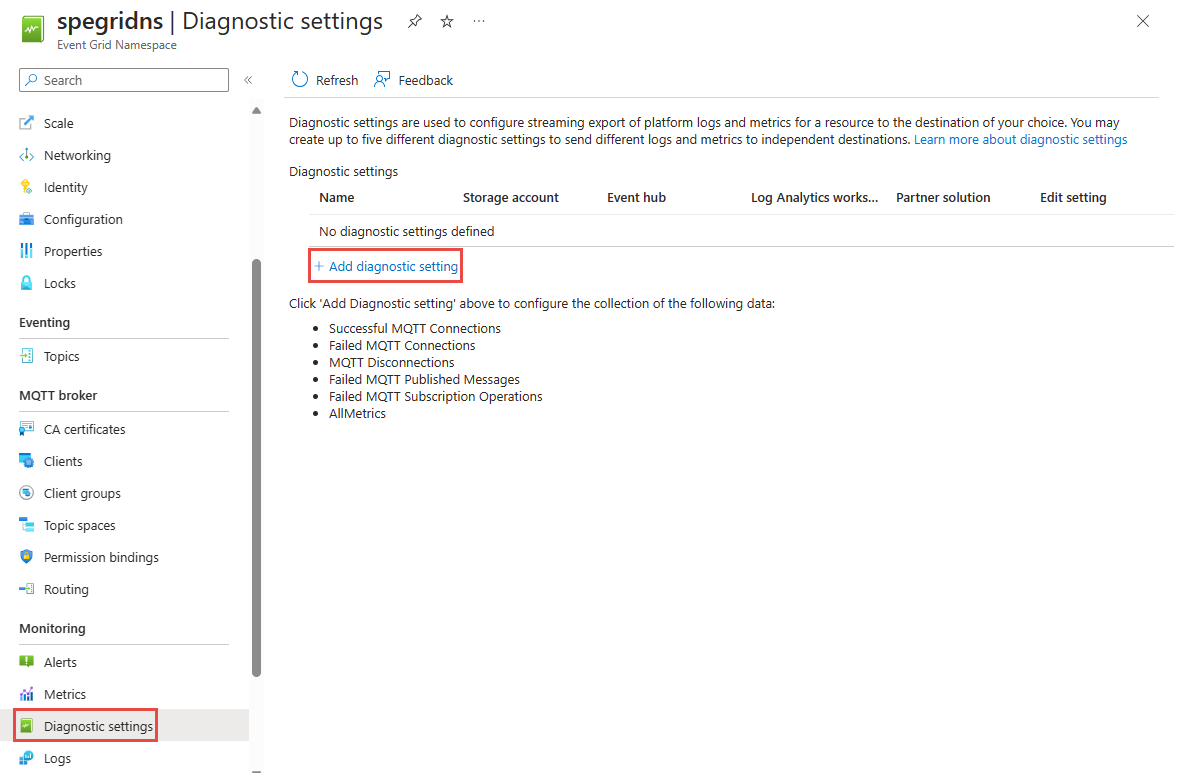
On the Diagnostic setting page, you can enable log categories as needed.
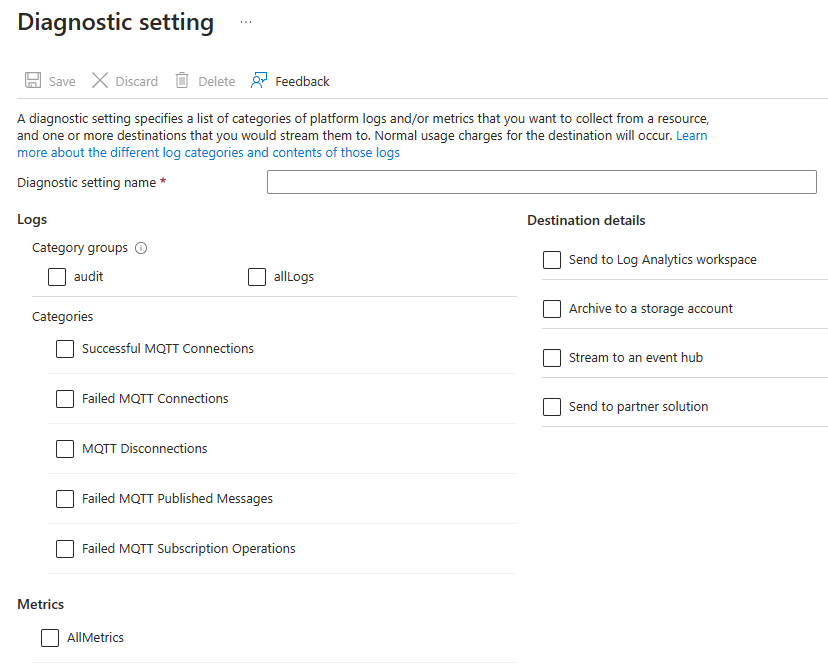
Once runtime logs are enabled, Event Grid starts collecting and storing them according to the diagnostic setting configuration.
Analyze runtime audit logsYou can analyze the collected runtime audit logs using the following sample query.
Connections report by session names
EGNSuccessfulMqttConnections | summarize count() by SessionNameAuthentication errors report by session name
EGNFailedMqttConnections | where ResultSignature == "AuthenticationError" | summarize count() by SessionNameHope this helps. Do let us know if you have any further queries.
-
Pawel Czop • 20 Reputation points
2025-03-22T20:27:22.4033333+00:00 I'm not interested in count, but error details: why authentication failed?
-
Khadeer Ali • 4,960 Reputation points • Microsoft External Staff
2025-03-24T10:49:52.86+00:00 Thanks for your clarification! Could you update your Kusto Query in Azure Monitor (Log Analytics Workspace) as follows:
EGNFailedMqttConnections | where ResultSignature == "AuthenticationError" | project Timestamp, SessionName, ClientId, FailureReason, Details | order by Timestamp descThis query will provide:
- Timestamp: When the authentication attempt occurred
- SessionName: Identifies the session
- ClientId: The MQTT client attempting to connect
- FailureReason: A short description of why authentication failed
- Details: Any additional information available
-
Pawel Czop • 20 Reputation points
2025-03-24T11:16:10.3266667+00:00 Thank you for your fast answer.
I tried to run the query, but it returns me the error:
'project' operator: Failed to resolve scalar expression named 'Timestamp'
Request id: 51ffc125-bdd1-4306-b27f-f55b81292d94
Could you please advice?
-
Khadeer Ali • 4,960 Reputation points • Microsoft External Staff
2025-03-24T11:33:49.5233333+00:00 Thank you for your patience. I appreciate your effort in running the previous query, and I sincerely apologize for the incorrect field names in my earlier response.I reverified the schema ref : egnfailedmqttconnections_Schema, please try the following updated Kusto query:
EGNFailedMqttConnections | where ResultSignature == "AuthenticationError" | project TimeGenerated, SessionName, ClientIdentity, AuthenticationType, Protocol, ResultDescription | order by TimeGenerated desc -
Khadeer Ali • 4,960 Reputation points • Microsoft External Staff
2025-03-25T11:31:09.65+00:00 Just checking to see if the above query works ?
-
Pawel Czop • 20 Reputation points
2025-03-25T11:54:12.7333333+00:00 yes, this worked. Thanks!
Logs appear when I use standard tools like MQTT Explorer or MQTTX, but nothing appears when I try to configure and connect from camera side.
The log I'm getting on camera side is:
Is there any possibility to look somewhere else what happened on server side in this case and what is the reason of error?
-
Khadeer Ali • 4,960 Reputation points • Microsoft External Staff
2025-03-27T06:24:13.8266667+00:00 Thanks for your patience. I’ve reached out to the Event Grid team, and they’re willing to investigate further. To help them check if the connection request reached the MQTT Broker, could you please provide the following details?
Event Grid Namespace Name:
Azure Region (Location):
Client ID / Client Authentication Name used while connecting:
Approximate time when the connection was attempted (including time zone):
Once I have this information, I’ll share it with the Event Grid team and update you as soon as I hear back. Appreciate your cooperation!
-
Khadeer Ali • 4,960 Reputation points • Microsoft External Staff
2025-03-28T18:04:01.7833333+00:00 Just following up to see if you had a chance to review my previous message. To assist you effectively, I would need a bit more information, such as:
Event Grid Namespace Name:Azure Region (Location):
Client ID / Client Authentication Name used while connecting:
Approximate time when the connection was attempted (including time zone):
Providing these details will help us pinpoint the issue and offer a solution promptly. Looking forward to your response!
-
Pawel Czop • 20 Reputation points
2025-03-30T18:41:34.11+00:00 Event Grid Namespace Name: iotcameraeventgrid1
Azure Region (Location): Germany West Central
Client ID / Client Authentication Name used while connecting:
- my-device
- client1
Approximate time when the connection was attempted (including time zone): 17:57 CET(for my-device), 18:28 CET(for client1)
CA Cert: Cert: DigiCertGlobalRootG3.crt.pem - downloaded from DigiCert
-
Pawel Czop • 20 Reputation points
2025-04-02T19:20:11.2366667+00:00 Any news related to more detailed logs? I forgot to add that date of connectionattempts was 30.03.2025
-
Khadeer Ali • 4,960 Reputation points • Microsoft External Staff
2025-04-03T11:45:56.2666667+00:00 @Pawel Czop ,
I have shared the information with the team, they are looking into it. Meanwhile could you let me know if this is registered in the EG Namespace? Also is the Client Cert and CA cert in line? -
Pawel Czop • 20 Reputation points
2025-04-05T13:03:18.28+00:00 this is registered in the EG Namespace?
Answer: I assume you are asking about the clients ,y-device and client1. Yes they are both registered
Also is the Client Cert and CA cert in line?
Answer:No, CA if from microsoft page(and used by Microsoft in Azure Grid service) It is from Cert: DigiCertGlobalRootG3
And works when I use it with cilent like MQTTX also with not related client cert.
-
Pawel Czop • 20 Reputation points
2025-04-07T09:32:00.4766667+00:00 Hi Ali,
I have setup port mirroring in th switch to capture the network traffic between camera and Azure Event Grid using WireShark.
I observed that regardless of the used certificate when camera sends Client hello message, then Azure doesn't respond with Server Hello message.
I found the similar issue with WolfSSL connection described here:
There it was potential reasone identified as Cipher Suites offered by the client in Client hello.
In my case camera offers the following:
It seems at least 4 are supported by Azure(referring to IoT Hub doc, as specific doc for Event Grid not yet exist).
Please investigate the issue and confirm if my hypothesis is correct?
Please also inform why server does not return Server Hello during TLS handshake?
-
Pawel Czop • 20 Reputation points
2025-04-07T09:36:55.22+00:00 Adding Wireshark logs as attachment of bigger imagesazure2.pngazure1.png
-
Khadeer Ali • 4,960 Reputation points • Microsoft External Staff
2025-04-10T09:31:33.7866667+00:00 We’ve reviewed the logs and found that the connection is failing due to the absence of a client authentication name in the CONNECT packet. When MQTT clients use X.509 certificate authentication, the client authentication name is typically provided in the Username field of the CONNECT packet.
Alternatively, the name can be extracted from the certificate itself if configured accordingly. However, in your case, the following was observed:
Client certificate info: X509Info { peer_cert: X509 { serial_number: "CA73E1F5171CB4807AAAA6CD3404A19F", issuer: [organizationName = "MqttBlogAppSamplesCA", commonName = "MqttBlogAppSamplesCA Intermediate CA"], subject: [commonName = "client1-authn-ID"], subject_alt_names: [client1-authn-ID], not_before: Mar 30 16:14:17 2025 GMT, not_after: Jul 8 16:14:10 2025 GMT }, peer_cert_chain: None }And the connection attempt resulted in the following error:
Connection attempt failed, error: Connect: Bad request: No client authentication name provided Result type: ClientError Signature: Connect-BadRequestYou can optionally choose to extract the client authentication name from the certificate itself by selecting one or more alternative sources below.
Action Required: Please update the client configuration to include the authentication name, typically passed in the Username field, and retry the connection.
Let us know once this is done .
-
Pawel Czop • 20 Reputation points
2025-04-10T10:31:01.6266667+00:00 Hi Ali,
Are you sure you analysed the proper connection attempt?
If yes, please provide me teh timestamp of the analysed network traffic in CET time.
Please be informed that I did some tests with the same ceritficate before a and after provided timings, with and wuthout user name.
But from camera I provided username.
Please also note my update of the case form 07.04, where I sent you the logs from Wireshark proving that Azure does not respond properly after 'Client Hello' message with 'Server Hello'.
This part is before sending CONNECT packet, because it is TLS handshake negotiation and Client sends it certificate after getting proper 'Server Hello'
Please double-check and confirm if you analysed my network logs.
-
Khadeer Ali • 4,960 Reputation points • Microsoft External Staff
2025-04-18T10:44:16.48+00:00 We followed up with our Product Group (PG) team regarding the issue, and here is the latest update:
For the past one week, all connect, publish, and subscribe operations against the “iotcamereventgrid1” namespace have been successful.
Could you please confirm if you are still experiencing the issue on your end? If not, we’ll consider the case resolved. Otherwise, we’re happy to continue investigating further based on your feedback.
-
Pawel Czop • 20 Reputation points
2025-04-18T11:50:46.6233333+00:00 Yes, I still experience the issue. And as metioned I provided you the logs which prove the problem. I asked for analysis TLS handskake with occurs BEFORE CONNECT and fails. What you see with CONNECT, publish and subscribe packets come NOT from camera but from MQTTX client tool.
The same issue was described in this post:
Conclusion was that(which is also present in my case) client does not send 'server_name' extension(SNI) in CLIENT HELLO packet for TLS handshake.
Can you confirm that it is mandatory to send this extension in CLIENT HELLO frame?
If yes, where it is written in Azure documentation?
-
Khadeer Ali • 4,960 Reputation points • Microsoft External Staff
2025-04-23T09:10:00.7833333+00:00 Thanks for your continued patience while we investigate this issue.
After further internal discussion and review, this appears to be related to SNI (Server Name Indication), which is a required component for TLS handshakes with Azure Event Grid MQTT Broker.
Please ensure that your intelligent camera is configured to send the correct SNI during the TLS handshake. This is commonly an issue with embedded devices or custom clients that do not include SNI in their request.
Team also in the process of updating the Event Grid TLS documentation, which will reflect this requirement shortly as part of the //Build 2025 updates.
Please try configuring the camera with the appropriate SNI and let us know if the issue persists.
Sign in to comment